Introduction
This design pattern for a security-centric IT environment is presented in the hope that it may be of some use to those wishing to implement a security-centric IT environment for a group of users (who require a high degree of security in order to carry out their responsibilities).
Please consider this a rough draft of an outline for the pattern; I will be evolving this pattern during the coming months to a more complete form (as time allows).
Any comments you care to make as to how this pattern can be improved upon or embellished for the good of all will be greatly appreciated!
Name
Phoenix
Intent
To ensure that users in an IT environment start their work sessions with PCs that are free of malware and updated with the latest updates, and to limit the attack window of malware on an infected PC to the duration of the user’s session on the infected PC.
Motivation
For many industries, it is imperative that users have access to an IT environment that is designed to provide them with effective protection against cyber-attacks by organized criminals and nation states engaged in industrial espionage.
However, this has become very difficult due to the evolution of malware that anti-virus software cannot detect; this makes it almost impossible to be certain that PCs are free of malware.
(See the article You Can’t Depend on Antivirus Software Anymore for more on why you cannot rely upon anti-virus software to detect and eradicate the latest strains of malware.)
This leads to another problem: most PCs run on a 24/7 basis. If a PC becomes infected with malware, it will usually have all the time it needs to accomplish its mission. For example, banking Trojans go into hiding and patiently wait for a victim to enter his or her credentials in order to gain access to sensitive accounts. And, given enough time, this will eventually happen.
The last problem we face is that it is nearly impossible to be certain that every PC in an IT environment has been updated with the latest application, operating system, and security updates. For example, if a PC has been infected, malware might prevent the PC from being updated. Or, more commonly, a PC might simply be switched off when it was supposed to be updated.
Thus, there are at least three problems that confront us when creating a secure IT environment for users:
- At any given time, you cannot be certain that PCs are not infected with malware.
- Malware that cannot be detected will probably survive long enough to accomplish its mission.
- You cannot be certain that PCs are updated with the latest application, operating system, and security updates.
The purpose of the Phoenix Design Pattern is to introduce compensating controls and procedures into an environment in order to significantly mitigate the risks and dangers posed by these three problems.
Applicability
Consider using the Phoenix Design Pattern in any industry where you must create a security-centric IT Environment.
In addition to others, this may include any or all of the following industries:
- Healthcare
- Financial Services
- Manufacturing
- Government
- Legal
- Defense
- Energy
- Transportation
Structure
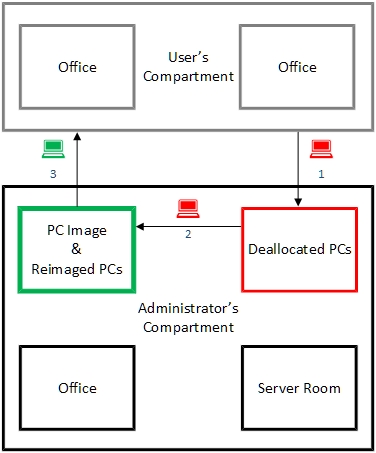
The structure associated with the Phoenix Design Pattern is a Secure Area that consist of the following secured compartments:
- User’s Compartment
- Administrator’s Compartment
- Compartment for Deallocated PCs
- Compartment for PC Image & Reimaged PCs
User’s Compartment
A secured compartment where Users carry out their responsibilities.
Administrators and Users have access to this compartment.
Administrator’s Compartment
A secured compartment where Administrators carry out their responsibilities.
Only Administrators have access to this compartment.
Compartment for Deallocated PCs
A secured compartment where deallocated PCs are quarantined; these PCs may be infected with malware and should be treated accordingly.
Only Administrators have access to this compartment.
Compartment for PC Image & Reimaged PCs
A secured compartment where the PC Image and reimaged PCs are stored.
Only Administrators have access to this compartment.
Participants
Administrator
An individual with administrative privileges.
User
An individual with responsibilities that require the use of a PC.
PC
A laptop or Stick PC required by a User to carry out his or her responsibilities.

PC Image
A system image that can be used to restore the persistent storage devices of a PC to a known state.
Collaborations
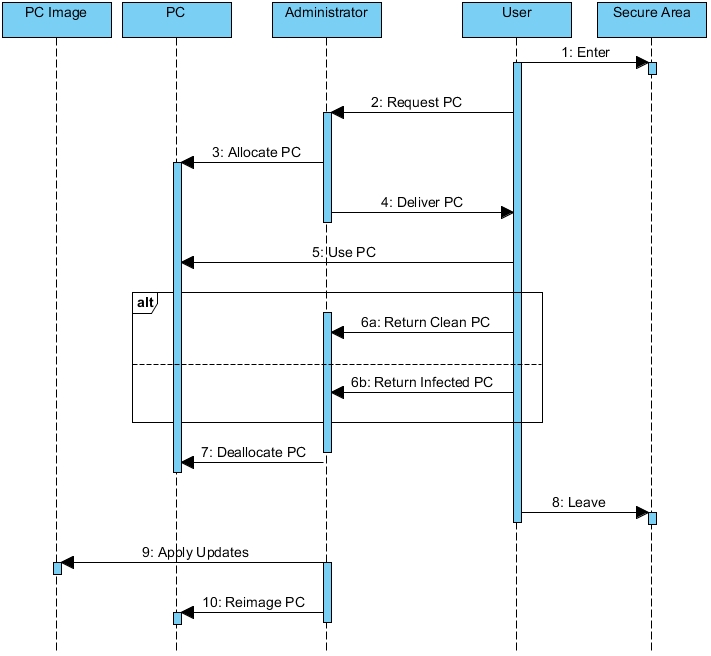
The minimum set of collaborations associated with the Phoenix Design Pattern include the following:
- User enters Secure Area
- User requests PC from Administrator
- Administrator allocates PC for User
- Administrator delivers PC to User
- User uses PC
- User returns PC to Administrator
- Administrator deallocates PC
- User leaves Secure Area
- Administrator applies Updates to PC Image
- Administrator reimages PC
Now we examine each collaboration in more detail.
User enters Secure Area
After presenting his or her credentials, the user is admitted to the Secure Area.
User requests PC from Administrator
After presenting his or her credentials, the User requests a PC from the Administrator.
Administrator allocates PC for User
After verifying the credentials of the User, the Administrator performs the following steps:
- Allocates a PC for the User
- Adds the PC to the List of Allocated PCs.
- Removes the allocated PC from the List of Available PCs.
- If necessary, whitelists the allocated PC’s MAC address
Administrator delivers PC to User
The Administrator removes the allocated PC from the Compartment for PC Image & Reimaged PCs and delivers it to the User in the User’s Compartment.
User uses PC
In order to begin a Work Session, the User will log in to the allocated PC.
User returns PC to Administrator
After completing a Work Session, the User will log out of the PC and return the PC to the Administrator.
At this point, the Administrator must assume the PC has the following properties:
- The PC has malware
- The PC is not updated with the latest operating system updates
- The PC is not updated with the latest application updates
- The PC is not updated with the latest security updates
Administrator deallocates PC
Upon receipt of the PC, the Administrator performs the following steps:
- Removes the PC from the List of Allocated PCs.
- Adds the PC to the List of Available PCs.
- As a precaution, blacklists the PC’s MAC address
- Quarantines the PC in the Compartment for Deallocated PCs
User leaves Secure Area
Normally, Users are not allowed to leave the Secure Area until it has been verified that they have returned the PC that was used during their Work Session.
If a user requires a PC for work outside of the Secure Area, the User must obtain permission and request a PC from the Administrator that has been configured with a greater degree of security and counter-measures against the loss or theft of the PC.
Administrator applies Updates to PC Image
At the end of a Work Cycle, the Administrator will perform the following tasks:
- Update the PC Image with the latest operating system updates
- Update the PC Image with the latest application updates
- Update the PC Image with the latest security updates
Administrator reimages PC
The Administrator must now perform the following tasks:
- If warranted, erase all data on the PC in accordance with secure data management practices and standards
- In the Administrator’s office, reimage the PC with a copy of the updated PC Image
- Store the PC in the Compartment for the PC Image & Reimaged PCs
At this point, the PC is ready for use by the next User.
Consequences
When a User begins a Work Session with his or her PC, the Administrator can be reasonably certain that:
- The PC is free of malware
- The PC is updated with the latest operating system updates
- The PC is updated with the latest application updates
- The PC is updated with the latest security updates
In addition, if the PC had been infected with malware before it was returned, the Administrator can be certain that the duration of the User’s Work Session on the infected PC would have placed an upper bound on the attack window, thus significantly limiting the time during which the malware would have been forced to accomplish its mission.
Implementation
There are many ways to implement this design pattern in a real IT environment; we have only presented the pattern in an outline form.
[There are many tools available that can automate the processes associated with the implementation of this pattern, many of them free of charge. These will be discussed in future versions of this article.]
Glossary
Work Session
The time interval during which an individual User performs work; logging in to a PC begins a Work Session and logging out ends a Work Session. (In most environments, the average length of a Work Session will be approximately 8 hours.)
Work Cycle
The time interval during which Users perform work on a cyclic basis. (In most environments, the length of a Work Cycle will be 24 hours.)
