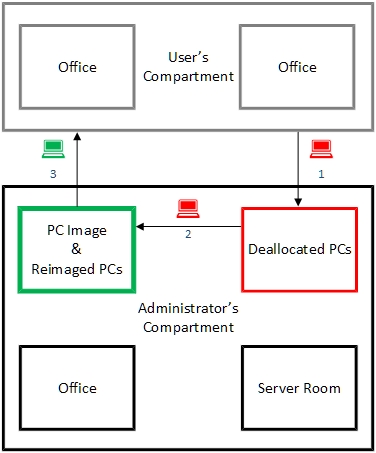
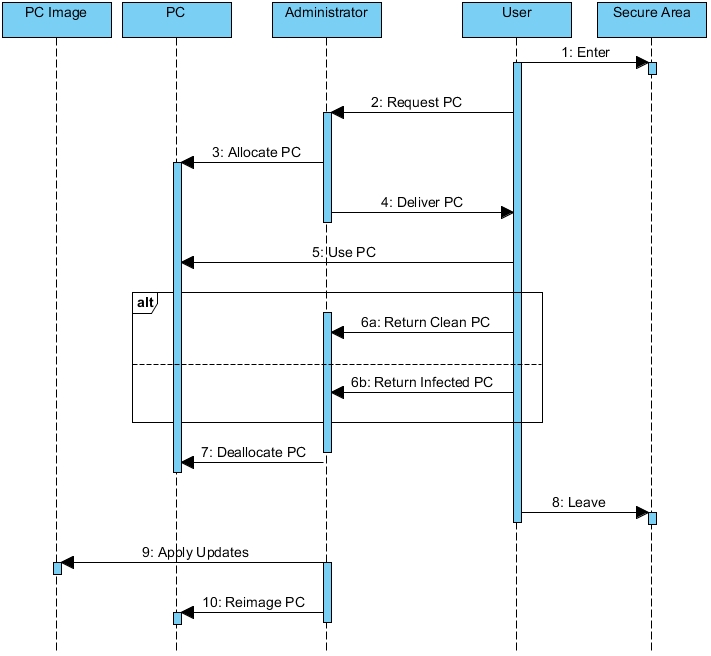
Confinet Security Model
In regard to security, Confinet meets the key objectives of confidentiality, integrity, and availabilty. However, Confinet goes far beyond the minimum standards that must be satisfied by a security system with a design that is also based upon the following core principles:
- Information is never automatically shared by default
- Information content can be dynamically updated at any time
- Information security permissions can be dynamically updated at any time
- Information is never stored or cached on a user’s persistent storage devices
- Information in transit is encrypted in accordance with the SSL/TLS protocols
- Information can be created, managed, protected, and shared within a single environment
The rationale and implications of these principals for information security are discussed below.
Information is never automatically shared by default.
The rationale for this principle in a system designed to protect confidential information and intellectual property is accountability. When individuals in an organization create confidential information which can be shared without their knowledge or consent, they cannot be held accountable for the security of the information they create for the organization.
Since Confinet was designed in accordance with this principle, the Confinet Client application never automatically shares information created by Confinet users with other Confinet users. In other words, in order for Confinet users to share information with other Confinet users, they must explicitly share the information they have created with Confinet.
In addition, the Confinet Admin application does not give Confinet Administrators access to information created by Confinet users; its only purpose is to administer Confinet groups and users.
Information content can be dynamically updated at any time.
The rationale for this principle in a system designed to protect confidential information and intellectual property is the ability to update information that is incorrect or out of date.
This is a necessary feature, since acting on information that is incorrect, or out of date, can have security ramifications. In short, preventing or controlling access to information that is incorrect is of little value to an organization.
Since Confinet was designed in accordance with this principle, the Confinet Client application allows Confinet users to dynamically update their documents and messages at any time. For example, if a Confinet user updates the contents of a message, the new contents will be seen the next time the recipients of the message open it.
Information security permissions can be dynamically updated at any time.
The rationale for this principle in a system designed to protect confidential information and intellectual property is the dynamic nature of privileged information concerning its classification and the nature of the roles individuals play in regard to its handling.
In many cases, the security classification of information is, for the most part, a function of time. For example, information that was considered confidential yesterday may be considered non-confidential today; or, information that was considered non-confidential yesterday may be considered confidential today.
Likewise, the nature of the roles that individuals play in regard to the handling of confidential information is usually a function of time. For example, individuals may be granted or denied access to sensitive information based upon their job titles, or the projects they participate in.
In recognition of this, the Confinet Client application allows Confinet users to dynamically update the permissions of their documents and messages. For example, if a Confinet user disables the view permission of a message, the message will not be seen the next time the recipients open a Message Browser window (or refresh the contents of existing Message Browser windows).
Information is never stored or cached on a user’s persistent storage devices.
A system designed to protect confidential information and intellectual property must protect against the loss or theft of user devices. The most effective way to achieve this objective is to prevent sensitive information from being stored or cached on user devices. Thus, the Confinet Client application never automatically stores information created by users on their persistent storage devices.
A Confinet user may elect to save one of their documents or messages on a persistent storage device; however, the Confinet Client application itself will not automatically store or cache user information on a persistent storage device (for example, a hard disk drive, or a USB Flash drive).
Information in transit is encrypted in accordance with the SSL/TLS protocols.
With more and more people working remotely, it is imperative that sensitive information be protected whenever it is transmitted over public networks.
It is also essential that information be protected whenever it is transmitted over an organization’s private networks. It is possible, however unlikely, that an organization’s private network could be compromised by an insider.
The Confinet product suite features always on encryption; information in transit is always encrypted, regardless of whether information is transmitted over a public or a private network.
Information can be created, managed, protected, and shared within a single environment.
Since Confinet is based upon this principal, the Confinet product suite allows the members of an organization to create, manage, protect, and share confidential information without recourse to any third-party applications.
The creation, management, protection, and sharing of confidential information within a single, managed environment is the most effective way to uniformly enforce security constraints placed upon confidential information.
If information is created, managed, and shared by separate applications, the security of the information will only be a strong as the security afforded it by the least secure of the applications handling the information.
The Confinet product suite eliminates this “weakest link” liability in the handling of sensitive information by providing a single environment wherein security constraints are uniformly applied to the handling of confidential information, from its inception and management, to its sharing with others and eventual retirement.
Conclusion
In regard to the creation, management, protection, and sharing of confidential information and intellectual property, the Confinet product suite is the only commercial offering that satisfies all of the principles enumerated and discussed above.