Confinet User Guide for Client 2.0
Adams Business Software Inc.
Copyright © 2016, 2017 by Adams Business Software Inc. All rights reserved.
Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the publisher was aware of a trademark claim, the designations have been printed with initial capital letters or in all capitals. The publisher and the author make no claim to these trademarks.
This document contains proprietary information of Adams Business Software Inc. It is provided under a license agreement and is protected by copyright law. The design and appearance of application windows, the design and appearance of dialog boxes, menu designs and their appearance, custom icon designs, and the arrangement and manipulation of application windows are creative expressions which are the intellectual property of Adams Business Software Inc. and protected by copyright law and international treaties.
The information contained in this publication does not include any product warranties, and any statements provided in this manual should not be interpreted as such.
Limit of Liability/Disclaimer of Warranty: While the publisher and author have used their best efforts in preparing this book, they make no representations or warranties with respect to the accuracy or completeness of the contents of this book and specifically disclaim any implied warranties of merchantability or fitness for a particular purpose. No warranty may be created or extended by sales representatives or written sales materials. The advice and strategies contained herein may not be suitable for your situation. You should consult with a professional where appropriate. Neither the publisher nor author shall be liable for any loss of profit or any other commercial damages, including but not limited to special, incidental, consequential, or other damages.
Confinet is a security software product suite that provides the members of an organization with everything they need in order to create, manage, protect, and share confidential information and intellectual property.
Confinet allows you to create documents and messages that can be shared with others
via the use of security mechanisms that give you precise control over who information is
shared with, how it is shared, and when it is shared.
In addition, Confinet has the following security-related objectives:
By definition, spam consists of useless, unsolicited, and unwanted messages. Since time
must be spent examining and then deleting spam, it is a drain on the productivity of an
organization.1
In addition, spam is commonly employed in phishing attacks, a form of cyber attack in
which an email with a malicious link is sent to a victim with the intent of tricking the
victim into clicking on the link, which then directs a browser to a site that can infect
the victim’s computer with malware.
Confinet combats spam by providing an organization with a confidential network. Only individuals with a Confinet account are able to communicate with the members of an organization via Confinet. This is in contrast to traditional email, which allows anyone to inundate an organization with spam from anywhere.
Malware2
is defined as “any software used to disrupt computer or mobile operations, gather
sensitive information, gain access to private computer systems, or display unwanted
advertising.” The main purpose of malware is to facilitate the theft of personal,
financial, or business information (including customer data).
Email may be the most effective tool used by cyber criminals to infect computers and
networks with malware. However, Confinet is insulated from this form of attack
because it does not make use of, or interact with, traditional email in any
way.
In addition, Confinet does not allow files of any type to be attached
to a message created with Confinet. Instead, Confinet allows users to
attach documents created with Confinet to messages created with
Confinet.3
The end result is that Confinet allows the members and affiliates of an organization to
communicate and share information without exposing them to the most common
sources of malware.
Thus, the adoption and use of Confinet by an organization is one of the single most effective things it can do to reduce its vulnerability to cyber attacks that rely upon malware to succeed.
If confidential information is handled by several applications, the security of the
information will be no greater than that provided by the least secure application that
handles the information.
Thus, if the least secure application that handles confidential information fails to protect it,
this may render the security features of the other applications that handle the information a
moot point.4
However, Confinet is a self-contained product suite that does not require the use of any untrusted, third-party applications to create, manage, protect, and share confidential information and intellectual property. The result is consistent and comprehensive coverage for the protection of confidential information, from its initial inception and creation to its dissemination to authorized users.
The Confinet product suite encrypts all transmitted information in accordance with the SSL/TLS protocols on both public and private networks. This always on encryption provides confidential information with protection on any network over which it is transmitted.
The Confinet Client application can be installed on many versions of the Windows, Mac OS X, and Linux operating systems. If you need administrator privileges to install the Confinet Client application, please seek the assistance of your System or Confinet Administrator.
The Confinet Client can be installed and run on a PC capable of running the following versions of the Windows operating system:
The Confinet Client can be installed and run on a Mac capable of running the following versions of the Mac OS X operating system:
You can install and run the Confinet Client on many versions of Linux that have Wine
1.6 or greater installed. (Wine is a compatibility layer capable of running Windows
applications on many versions of Linux.)
The Confinet Client application can be compiled and run as a native application on many versions of the Linux operating system, including Red Hat Enterprise Linux, SUSE Linux Enterprise, and Ubuntu. If you need to run the Confinet Client application as a native application on Linux, please contact us in order to discuss your requirements.
The Confinet Client application can be compiled and run as a native application on Oracle Solaris 11. If you need to run the Confinet Client application as a native application on Oracle Solaris 11, please contact us in order to discuss your requirements.
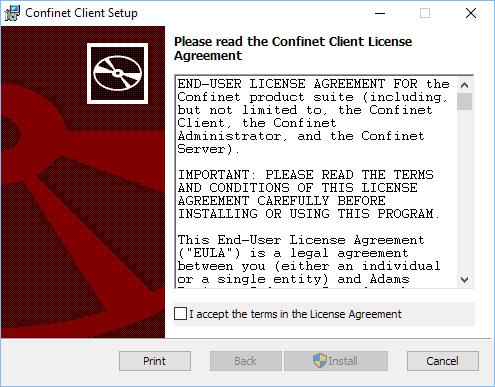
Unless your organization has instructed you otherwise, you may download and install
the latest version of the Confinet Client application installation file from the
Confinet website (www.confinet.us).
If you need to verify the authenticity of a Confinet installation file, you can do so by computing the SHA-1 hash value of the installation file and comparing it with the value posted on the Confinet web site (confinet.us/support/confinet-product-hashes).
(See figure 2.1)
To install the Confinet Client application on Windows:
To install the Confinet Client application on Mac OS X:
The Confinet Security Model is based upon the following core principles:
The rationale and implications of these principals are discussed below.
Information is never automatically shared by default.
The rationale for this principle in a system designed to protect confidential information
and intellectual property is accountability. When individuals in an organization create
confidential information which can be shared without their knowledge or consent, they
cannot be held accountable for the security of the information they create for the
organization.
Since Confinet was designed in accordance with this principle, the Confinet Client
application never automatically shares information created by Confinet users with
other Confinet users. In other words, in order for Confinet users to share information
with other Confinet users, they must explicitly share the information they have created
with Confinet.
In addition, the Confinet Admin application does not give Confinet Administrators access
to information created by Confinet users; its only purpose is to administer
Confinet groups and users.
Information content can be dynamically updated at any time.
The rationale for this principle in a system designed to protect confidential information
and intellectual property is the ability to update information that is incorrect or out of
date.
This is a necessary feature, since acting on information that is incorrect, or out
of date, can have security ramifications. In short, preventing or controlling
access to information that is incorrect or out of date is of little value to an
organization.
Since Confinet was designed in accordance with this principle, the Confinet Client
application allows Confinet users to dynamically update their documents and
messages at any time. For example, if a Confinet user updates the contents of a
message, the new contents will be seen the next time the recipients of the message open
it.
Information security permissions can be dynamically updated at any time.
The rationale for this principle in a system designed to protect confidential information
and intellectual property is the dynamic nature of privileged information concerning
its classification and the nature of the roles individuals play in regard to its
handling.
In many cases, the security classification of information is, for the most part, a function
of time. For example, information that was considered confidential yesterday may be
considered non-confidential today; or, information that was considered non-confidential
yesterday may be considered confidential today.
Likewise, the nature of the roles that individuals play in regard to the handling of confidential
information is usually a function of time. For example, individuals may be granted or denied
access to sensitive information based upon their job titles, or the projects they participate
in.1
In recognition of this, the Confinet Client application allows Confinet users to
dynamically update the permissions of their documents and messages. For
example, if a Confinet user disables the view permission of a message, the
message will not be seen the next time the recipients open a Message Browser
window (or refresh the contents of an existing Message Browser window).
2
Information is never stored or cached on a user’s persistent storage devices.
A system designed to protect confidential information and intellectual property must
protect against the loss or theft of user devices. The most effective way to achieve this
objective is to prevent sensitive information from being stored or cached on
user devices. Thus, the Confinet Client application never automatically stores
information created by users on their persistent storage devices.
A Confinet user may elect to save one of their documents or messages on a persistent
storage device; however, the Confinet Client application itself will not automatically
store or cache user information on a persistent storage device (for example, a hard disk
drive, or a USB Flash drive).
Information in transit is encrypted in accordance with the SSL/TLS protocols.
With more and more people working remotely, it is imperative that sensitive
information be protected whenever it is transmitted over public networks.
It is also essential that information be protected whenever it is transmitted over an
organization’s private networks. It is possible, however unlikely, that an organization’s
private network could be compromised by an insider.
The Confinet product suite features always on encryption; information in transit is
always encrypted, regardless of whether information is transmitted over a public or a
private network.
Information can be created, managed, and protected within in a single environment.
Since Confinet is based upon this principal, the Confinet product suite allows the
members of an organization to create, manage, protect, and share confidential
information without recourse to any third-party applications.
The creation, management, protection, and sharing of confidential information within a
single, managed environment is the most effective way to uniformly enforce security
constraints placed upon confidential information.
If information is created, managed, and shared by separate applications, the security of
the information will only be as strong as the security afforded it by the least secure of
the applications handling the information.
The Confinet product suite eliminates this “weakest link” liability in the handling of sensitive information by providing a single environment wherein security constraints are uniformly applied to the handling of confidential information.3
Unlike many security models, the Confinet Security Model employs familiar metaphors
and was designed to be used by everyone in an organization, not just those with a
technical background.
The Confinet Security Model employs just eight basic concepts that can be easily
understood and applied to the protection of confidential information and intellectual
property.
The basic concepts employed by the Confinet Security Model are listed below:
These basic concepts, as employed by the Confinet Security Model, are described in the following sections.
A user is an individual with a Confinet account, created by a Confinet Administrator.
A group is a collection of users.
A document is used to create, manage, and share information on a per user basis.
A message is used to create, manage, and share information on a per group7 basis.
Messages are normally sent to other users; however, this is not always the case.10
A folder contains documents and subfolders.
A document key allows the owner of a document to grant access to another user.
A document keyring is the collection of all document keys for a particular document.
A folder key allows the owner of a folder to grant access to another user.
A folder keyring is the collection of all folder keys for a particular folder.
A group key grants a user access to the members of a group.
A group keyring is the collection of all group keys for a particular group.
The Confinet Client application provides the members of an organization with
everything they need to create, manage, protect, and share confidential information and
intellectual property.
In order to accomplish this, the Confinet Client application is composed of a set of
components that allow the members of an organization to accomplish these
tasks.
The main components of the Confinet Client application are listed below:
The following sections provide a functional overview of these components.
(See figure 4.1)
The Console window allows you to perform the following tasks:
(See figure 4.2)
A My Groups window allows you to perform the following tasks:
(See figure 4.3)
A Message Browser window allows you to perform the following tasks:
(See figure 9.9)
A Message Editor window allows you to perform the following message related tasks:
(See figure 9.8)
A Message Reader window allows you to perform the following message related tasks:
(See figure 4.6)
A Document Browser window allows you to perform the following tasks:
(See figure 4.7)
A Document Editor window allows you to perform the following tasks:
If you have a document key for a document created by another user, a Document Reader window can allow you to perform the following tasks:
(See figure 4.8)
Every document you create has an associated document keyring.
A document keyring is the collection of all document keys for a particular
document.
A Document Keyring window allows you to perform the following tasks:
(See figure 4.9)
Every folder you create has an associated folder keyring.
A folder keyring is the collection of all folder keys for a particular folder.
A Folder Keyring window allows you to perform the following tasks:
(See figure 4.10)
A My Document Keyring window allows you to view the document keys created for
you.
A My Document Keyring window allows you to perform the following tasks:
(See figure 4.11)
A My Folder Keyring window allows you to view the folder keys created for
you.
A My Folder Keyring window allows you to perform the following tasks:
Confinet lets you create documents that can display formatted text, tables, bullet lists,
pictures, and more.
This chapter will discuss the following tasks:
To create a document in a Document Browser window:
To rename a document in a Document Browser window:
To delete a document in a Document Browser window:
(See figure 5.7)
To edit the contents of a document, open the document in a Document Editor window. Use the Document Editor window Edit menu to perform basic editing tasks.
From the Edit menu, click Undo.
From the Edit menu, click Redo.
From the Edit menu, click Cut.
From the Edit menu, click Copy.
From the Edit menu, click Paste.
From the Edit menu, click Select All.
(See figure 5.8)
Select the font style and weight from the Formatting toolbar.
To make the selected text bold, click Format Bold  in the Formatting
toolbar.
in the Formatting
toolbar.
To make the selected text italic, click Format Italic  in the Formatting
toolbar.
in the Formatting
toolbar.
To underline the selected text, click Underline  in the Formatting toolbar.
in the Formatting toolbar.
To change the font of the selected text, select the font name from the Font Name list in the Formatting toolbar.
To change the font size of the selected text, select the font size from the Font Size list in the Formatting toolbar.
Selected text can be aligned flush left, centered, flush right, or justified.
To align the selected text flush left, click Align Left  in the Formatting
toolbar.
in the Formatting
toolbar.
To center the selected text, click Align Center  in the Formatting toolbar.
in the Formatting toolbar.
To align the selected text flush right, click Align Right  in the Formatting
toolbar.
in the Formatting
toolbar.
To justify the selected text, click Align Justified  in the Formatting
toolbar.
in the Formatting
toolbar.
You can increase or decrease the indentation of selected text.
To increase the indentation of the selected text, click Increase Indent  in the
Formatting toolbar.
in the
Formatting toolbar.
To decrease the indentation of the selected text, click Decrease Indent  in the
Formatting toolbar.
in the
Formatting toolbar.
To change the color of the selected text, select the color from the Font Color list in the Formatting toolbar.
(See figure 5.9)
From the Insert menu, you can insert lists with one of the following styles:
From the Insert menu, you can insert a line by clicking Line.
(See figure 5.10)
To insert a table:
After you insert a table, you can increase or decrease its rows and columns to suit your needs.
To insert a reference to a picture file into a document:
(See figure 5.11)
From the Format menu, you can format text as one of the following lists:
You can also remove list formatting by clicking No Text List.
(See figure 5.12)
The Document Editor window Table menu allows you to perform the following operations:
(See figure 5.13)
To search for text in a document:
(See figure 5.14)
To find and replace text in a document:
(See figure 5.15)
To check and correct spelling errors in a document:
You can view any revision of any document you have created.
To view document revisions from the View menu, click Revision History for
document name.
To view the contents of a revision of the document, click on the revision date.
After you open a document in a Document Editor window, you can print its contents.
(See figure 5.18)
To print the contents of a document:
(See figure 5.19)
To preview the contents of a document:
 .
.After you open a document in a Document Editor window, you can export its contents to a text file or a PDF file.
To export the contents of a document to a text file:
To export the contents of a document to a PDF file:
From the Console window, you can restore any document you have
deleted.1
To restore a document you have deleted:
Note that, by default, the latest version of the document will be restored in the original
folder that contained it.
If the original folder containing the document has been deleted, you will be given the option to select an existing folder in which to restore the document.
The purpose of a document key is to allow users to share their documents with other
users in a secure manner.
A document key is associated with the following:
The owner of a document creates a document key for the document in order to share
the contents of the document with another user: the document key holder.
At any given point in time, the state of a document key is either active or inactive. If a document key is inactive, the contents of the document associated with it cannot be viewed by the document key holder.1
The permissions associated with a document key determine what the document
key holder is allowed to do with the contents of the document associated with the
document key.
In order to meet the demands of real-world use cases, document keys grant (or deny) the following permissions in regard to the contents of the document associated with a document key:
| Permission | Group |
| Allow the contents of the document to be viewed | lossless |
| Allow the contents of the document to be updated | lossless |
| Allow the contents of the document to be copied from the clipboard | lossless |
| Allow the contents of the document to be copied to the clipboard | lossy |
| Allow the contents of the document to be exported to a text file | lossy |
| Allow the contents of the document to be exported to a PDF file | lossy |
| Allow the contents of the document to be printed | lossy |
| Allow the contents of the document to be searched | lossless |
These permissions are divided into two groups: lossy and lossless. In this context, the terms
lossy2
and lossless refer to a permission’s potential impact on information security.
If you enable lossy permissions for document key holders, you explicitly give them a
means by which they can easily convey the contents of the document associated with a
document key to others without your knowledge or authorization.
By contrast, enabling lossless permissions does not give document key holders an
explicit means by which they can easily convey information to unauthorized
parties.3
The various document key permissions are described in detail below.
Allow the contents of the document to be viewed. If this permission is enabled, the
document key holder can view the contents of the document. Note: Unless this
permission is enabled, any other permission will be irrelevant and ignored.
Allow the contents of the document to be updated. If this permission is enabled, the
document key holder will be allowed to update the contents of the document. Note:
Unless this permission is enabled, any other permission that would allow the contents of
the document to be updated in any way will be ignored.
Allow the contents of the document to be copied from the clipboard. If this
permission is enabled, the document key holder will be allowed to modify the
document by pasting the contents of the clipboard into the document at a desired
location.
Allow the contents of the document to be copied to the clipboard. If this lossy permission
is enabled, the document key holder will be allowed to copy the contents of the
document to the clipboard. CAUTION: The owner of the document should
take care when enabling this permission, since it could allow the document
key holder to use the clipboard to copy the contents of the document to a
file or third-party application (for example, an email client) for distribution
to others without authorization.
Allow the contents of the document to be exported to a text file. If this lossy
permission is enabled, the document key holder will be allowed to export the
contents of the document to a text file. CAUTION: The owner of the
document should take care when enabling this permission, since it
could allow the document key holder to export the contents of the
document to an editable text file for distribution to others without
authorization.
Allow the contents of the document to be exported to a PDF file. If this lossy
permission is enabled, the document key holder will be allowed to export the contents
of the document to a PDF file. CAUTION: The owner of the document should
take care when enabling this permission, since it could allow the document
key holder to export the contents of the document to a PDF file for
distribution to others without authorization.
Allow the contents of the document to be printed. If this lossy permission is enabled, the
document key holder will be allowed to print the contents of the document.
CAUTION: The owner of the document should take care when enabling
this permission, since it could allow the document key holder to print the
contents of the document and then distribute the printed material to others
without authorization.
Allow the contents of the document to be searched. If this permission is enabled, the document key holder will be allowed to search the contents of the document using full text-search capabilities.4
The attributes of a document key determine when, where, and how a document key can be accessed by the document key holder. A document key has the following attributes:
| Active months of the year | optional |
| Active days of the week | optional |
| Active hours of the day (including time zone) | optional |
| Session duration | optional |
| Expiration date | mandatory |
| Passcode | optional |
| Document version | optional |
Of these attributes, only the document key expiration date is mandatory.
These attributes are described below.
Active months of the year. This attribute allows the owner of the document to specify
the months of the year during which the document key is active.
Active days of the week. This attribute allows the owner of the document to specify the
days of the week on which the document key is active.
Active hours of the day. This attribute allows the owner of the document to specify the
hours of the day during which the document key is active, including the time
zone.
Session duration. This attribute allows the owner of the document to specify a session
duration for the document key. A session duration is specified in minutes or seconds and
controls the amount of time the document can be displayed after it has been opened by
the document key holder. Once the session duration expires, the document will be
automatically closed.
Expiration date. Every document key must have an expiration date. After the
expiration date of a document key has been reached, the document key will become
inactive.5
Passcode. The owner of a document can associate a passcode with a document
key. If this is done, the document key holder will need to enter the passcode
before he or she can open the document that is associated with the document
key.
Document revision. By default, the current version of a document is associated with a document key. However, the owner of a document can associate a previous revision of a document with a document key. In this case, since any previous version of a document cannot be changed, any permissions that would allow the document key holder to update the contents of the document will be ignored.
This section will discuss how you can view document keys created for you by
others.
The My Document Keyring window allows you to view the permissions and attributes
associated with document keys created for you by others.
To view document keys created for you by others:
Click on the column headers to sort the document keys by any of the following:
From the File menu, click Open Document to open the document associated with the currently selected document key.
This section will discuss how you can create document keys for others.
Creating a document key for a document involves the following steps:
Most of these steps are optional and have reasonable default values.
The following sections illustrate each of these steps.
In order to create a document key for a document, you must first open the document
keyring associated with the document.
To open the document keyring associated with a document:
To start the Create Document Key wizard:
(See figure 6.6)
This page of the Create Document Key wizard allows you to select the version of the
document to be associated with the document key.
To associate the document key with the current (latest) version of the document, click
Current version.
To associate a previous version of the document with the document key, click Previous
version, and then select the previous version of the document you want to associate
with the document key.
To proceed to the next step, click Next.
(See figure 6.7)
This page of the Create Document Key wizard allows you to select the permissions that
will be granted to the document key holder.
These permissions allow the contents of the document to be viewed, updated, copied
from the clipboard, copied to the clipboard, exported to a text file, exported to a PDF file,
printed, or searched.
To proceed to the next step, click Next.
(See figure 6.8)
This page of the Create Document Key wizard allows you to select the active status of
the document key.
A document key can be active or inactive; however, only an active document key will
grant the document key holder access to the document associated with the document
key.
To create an active document key, select Enable active status; to create a document
key that is initially inactive, clear Enable active status.
To proceed to the next step, click Next.
(See figure 6.9)
This page of the Create Document Key wizard allows you to select the months of the
year during which the document key will be active.
To proceed to the next step, click Next.
(See figure 6.10)
This page of the Create Document Key wizard allows you to select the days of the week
on which the document key will be active.
To proceed to the next step, click Next.
(See figure 6.11)
This page of the Create Document Key wizard allows you to select the hours of the day
during which the document key will be active, including the timezone.
To proceed to the next step, click Next.
(See figure 6.12)
This page of the Create Document Key wizard allows you to specify a session duration
for the document key.
A session duration determines the amount of time the document may be viewed
during one session (a session begins immediately after the document has been
opened).
After the session duration has elapsed, the document will be automatically
closed.
To proceed to the next step, click Next.
(See figure 6.13)
This page of the Create Document Key wizard allows you to select an expiration date
for the document key.
After the expiration date of a document key has been reached, the document
key becomes inactive.
To proceed to the next step, click Next.
(See figure 6.14)
This page of the Create Document Key wizard allows you to specify a
passcode6
for the document key.
If you specify a passcode for a document key, the document key holder will need to
enter the passcode before the document associated with the document key can be
accessed.
To proceed to the next step, click Next.
(See figure 6.15)
This page of the Create Document Key wizard allows you to select the users for whom
a copy of the document key will be created.
You can select users from either your home groups or your personal groups.
To proceed to the next step, click Next.
(See figure 6.16)
This page of the Create Document Key wizard allows you to confirm your
selections.
If you have selected one user, click Finish to create a document key for the user based
upon your selections.
If you have selected more than one user, click Finish to create a document key for each
user based upon your selections.
The new document keys will be displayed in the Document Keyring window.
You can update the permissions and attributes of document keys at any time.
Specifically, you can update any of the following:
(See figure 6.17)
To update the document version associated with a document key:
(See figure 6.18)
To update the permissions associated with a document key:
(See figure 6.19)
To update the active status of a document key:
(See figure 6.20)
To update the active months of a document key:
(See figure 6.21)
To update the active days of a document key:
(See figure 6.22)
To update the active hours of a document key:
(See figure 6.23)
To update the session duration of a document key:
(See figure 6.24)
To update the expiration date of a document key:
(See figure 6.25)
To update the passcode of a document key:
(See figure 6.26)
To delete a document key:
Note: You cannot undo this operation.
Folders can be used to create a hierarchical organization for your documents.
(See figure 7.1)
To create a folder:
(See figure 7.2)
To rename a folder:
(See figure 7.3)
To delete a folder:
Note: You cannot undo this operation.1
(See figure 7.4)
To search for documents in a folder:
Note: Document content is indexed once every hour. If you have recently updated the contents of a document, you may need to wait3 until the new contents have been indexed before you can search for the document based upon its updated contents.
The purpose of a folder key is to allow users to share their folders with other users in a
secure manner.
A folder key is associated with the following:
The owner of a folder creates a folder key for the folder in order to share the contents
of the folder with another user: the folder key holder.
At any given point in time, the state of a folder key is either active or inactive. If a folder key is inactive, the contents of the folder associated with it cannot be viewed by the folder key holder.1
The permissions associated with a folder key determine what the folder key holder
is allowed to do with the contents of the folder associated with the folder
key.
Folder keys grant (or deny) the following permissions in regard to the contents of the folder associated with a folder key:
| Permission | Group |
| Allow the contents of the folder to be viewed | lossless |
| Allow the contents of the folder to be searched | lossless |
The various folder key permissions are described in detail below.
Allow the contents of the folder to be viewed. If this permission
is enabled, the folder key holder can view the contents of the
folder.2
Allow the contents of the folder to be searched. If this permission is enabled, the folder key holder will be allowed to search the contents of the folder for documents3 using full text-search capabilities.
The attributes of a folder key determine when, where, and how a folder key can be accessed by the folder key holder. A folder key can have the following attributes:
| Active months of the year | optional |
| Active days of the week | optional |
| Active hours of the day (including time zone) | optional |
| Session duration | optional |
| Expiration date | mandatory |
| Passcode | optional |
Of these attributes, only the folder key expiration date is mandatory.
The folder key attributes are described below.
Active months of the year. This attribute allows the owner of the folder to specify the
months of the year during which the folder key is active.
Active days of the week. This attribute allows the owner of the folder to specify the
days of the week on which the folder key is active.
Active hours of the day. This attribute allows the owner of the folder to specify
the hours of the day during which the folder key is active, including the time
zone.
Session duration. This attribute allows the owner of the folder to specify a session
duration for the folder key. A session duration is specified in minutes or seconds and
controls the amount of time the folder can be displayed after it has been opened by the
folder key holder. Once the session duration expires, the folder will be automatically
closed.
Expiration date. Every folder key must have an expiration date. After the
expiration date of a folder key has been reached, the folder key will become
inactive.4
Passcode. The owner of a folder can associate a passcode with a folder key. If this is done, the folder key holder will need to enter the passcode before he or she can open the folder that is associated with the folder key.
This section will discuss how you can view folder keys created for you by others.
The My Folder Keyring window allows you to view the permissions and attributes
associated with the folder keys created for you by others.
To view the folder keys created for you by others:
Click on the column headers to sort the folder keys by any of the following:
From the File menu, click Open Folder to open the folder associated with the currently selected folder key.
This section will discuss how you can create folder keys for others.
Creating a folder key for a folder involves the following steps:
Most of these steps are optional and have reasonable default values.
The following sections illustrate each of these steps.
In order to create a folder key for a folder, you must first open the folder
keyring associated with the folder.
To open the folder keyring associated with a folder:
(See figure 8.4)
To start the Create Folder Key wizard:
(See figure 8.5)
This page of the Create Folder Key wizard allows you to select the permissions that will
be granted by the folder key.
These permissions allow the contents of the folder to be viewed or searched.
To proceed to the next step, click Next.
(See figure 8.6)
This page of the Create Folder Key wizard allows you to select the status of the folder
key.
A folder key can be active or inactive; however, only an active folder key can be used to
grant access to a folder.
To create an active folder key, select Enable active status.
To proceed to the next step, click Next.
(See figure 8.7)
This page of the Create Folder Key wizard allows you to select the months of the year
during which the folder key will be active.
To proceed to the next step, click Next.
(See figure 8.8)
This page of the Create Folder Key wizard allows you to select the days of the week on
which the folder key will be active.
To proceed to the next step, click Next.
(See figure 8.9)
This page of the Create Folder Key wizard allows you to select the hours of the day
during which the folder key will be active.
To proceed to the next step, click Next.
(See figure 8.10)
This page of the Create Folder Key wizard allows you to specify a session duration for
the folder key.
A session duration determines the amount of time the folder may be viewed
during one session (a session begins immediately after the folder has been
opened).
After the session duration has elapsed, the folder will be automatically closed.
To proceed to the next step, click Next.
(See figure 8.11)
This page of the Create Folder Key wizard allows you to select an expiration date for
the folder key.
After the expiration date of a folder key has been reached, the folder key becomes
inactive.
To proceed to the next step, click Next.
(See figure 8.12)
This page of the Create Folder Key wizard allows you to specify a passcode for the folder
key.5
If you specify a passcode for a folder key, the user will need to enter the passcode before
the folder associated with the folder key can be accessed.
To proceed to the next step, click Next.
(See figure 8.13)
This page of the Create Folder Key wizard allows you to select the users for whom a
copy of the folder key will be created.
To proceed to the next step, click Next.
This page of the Create Folder Key wizard allows you to confirm your selections.
To create the folder key (or folder keys), click Finish.
After the folder keys have been created, they will be displayed in the Folder Keyring window.
You can update the permissions and attributes of folder keys at any time.
Specifically, you can update any of the following:
(See figure 8.16)
To update the permissions associated with a folder key:
(See figure 8.17)
To update the active status of a folder key:
(See figure 8.18)
To update the active months of a folder key:
(See figure 8.19)
To update the active days of a folder key:
(See figure 8.20)
To update the active hours of a folder key:
(See figure 8.21)
To update the session duration of a folder key:
(See figure 8.22)
To update the expiration date of a folder key:
(See figure 8.23)
To update the passcode of a folder key:
(See figure 8.24)
To delete a folder key:
Note: You cannot undo this operation.
Confinet lets you create messages that can display formatted text, tables, bullet lists, pictures, and more.
Every message has a set of message permissions associated with it.
Message permissions allow you to control what the recipients of a message are
allowed to do with the contents of a message and how they can respond to a
message.
As in the case of document key permissions, message permissions are divided into two
groups: lossy and lossless. In this context, the terms lossy and lossless refer to the
potential disclosure of information to unauthorized parties.
If you enable lossy permissions for a message, you explicitly give the recipients of a message a
means by which they can easily convey the contents of the message to others without your explicit
authorization.1
By contrast, enabling lossless permissions does not give the recipients of a message an
explicit means by which they can easily convey information to unauthorized
parties.
Furthermore, there are two types of message permissions: message content permissions and message user permissions; both of these types of permissions are described in the following sections.
Message content permissions determine what the recipients of a message are allowed to
do with the contents of a message.
The following message content permissions can be enabled or disabled:
| Permission | Group |
| Allow the contents of the message to be viewed | lossless |
| Allow the contents of the message to be copied to the clipboard | lossy |
| Allow the contents of the message to be exported to a text file | lossy |
| Allow the contents of the message to be exported to a PDF file | lossy |
| Allow the contents of the message to be printed | lossy |
| Allow the contents of the message to be searched | lossless |
Message content permissions are described in detail below.
Allow the contents of the message to be viewed. If this permission is enabled, the
recipients of the message can view its contents. Note: Unless this permission is enabled,
any other permission will be irrelevant and ignored.
Allow the contents of the message to be copied to the clipboard. If this lossy permission
is enabled, the recipients of the message will be allowed to copy the contents of the
message to the clipboard. CAUTION: The creator of a message should take
care when enabling this permission, since it could allow message recipients
to use the clipboard to copy the contents of the message to a file or
third-party application (for example, an email client) for distribution to
others without authorization.
Allow the contents of the message to be exported to a text file. If this lossy permission is
enabled, message recipients will be allowed to export the contents of the message to a
text file. CAUTION: The creator of a message should take care when
enabling this permission, since it could allow message recipients to export
the contents of the message to a text file for distribution to others without
authorization.
Allow the contents of the message to be exported to a PDF file. If this lossy permission
is enabled, message recipients will be allowed to export the contents of the message to
a PDF file. CAUTION: The creator of a message should take care when
enabling this permission, since it could allow message recipients to export
the contents of the message to a PDF file for distribution to others without
authorization.
Allow the contents of the message to be printed. If this lossy permission is enabled,
message recipients will be allowed to print the contents of the message. CAUTION:
The creator of a message should take care when enabling this permission,
since it could allow message recipients to print the contents of the
message and then distribute the printed material to others without
authorization.
Allow the contents of the message to be searched. If this permission is enabled, message recipients will be allowed to search the contents of the message using full text-search capabilities.
Message user permissions determine how message recipients are allowed to reply to a
message.
The following message user permissions can be enabled or disabled:
| Permission | Group |
| Allow reply | lossy |
| Allow reply to all | lossy |
| Allow forward to others | lossy |
Message content permissions are described as follows.
Allow reply. If this lossy permission is enabled, the recipients of the message will be
allowed to reply directly to the sender of the message. However, enabling this permission
allows the recipients of the message to potentially send the message to other users as
well.
Allow reply to all. If this lossy permission is enabled, the recipients of the message will
be allowed to reply directly to all of the recipients of the message. However, enabling
this permission allows the recipients of the message to potentially send the message to
other users as well.
Allow forward to others. If this lossy permission is enabled, the recipients of the
message will be allowed to forward the message to other users.
CAUTION: The creator of a message should take care when enabling any
message user permissions, since they could allow message recipients to
send the message to other users without the knowledge of the message
creator.
Note: Selecting the Message read-only check box when creating a message will disable all lossy permissions by default, including message user permissions.
You can create a message in a Message Browser window.
To create a new message:
After you create a new message, you will be given the opportunity to add message content, recipients, and attachments.
(See figure 9.4)
The Message Editor window has all of the features of the Document Editor
window and is identical in terms of functionality.
See the section editing documents for information on general editing tasks when
composing the contents of a message.
See the section document spelling for information on spell checking the contents of a message.2
(See figure 9.5)
To select the primary recipients of a message, click To.
To select the secondary recipients of a message, click Cc.
To select the tertiary3 recipients of a message, click Bcc.
When you create a message, you can attach any of your documents to the message.
However, remember that the recipients of your message must have document keys in
order to access the attached documents.
To attach a document to a message, click Add Document.
To remove a document attachment, click Remove Document.
To verify that your message recipients have document keys for the attached documents,
click Verify Documents.
If a message recipient does not have a document key for an attached document, you will be prompted to create a document key for the user; as shown below:
(See figure 9.8)
In a Message Reader window, you can view messages created for you by other
users.
To view a message created for you:
Depending upon the permissions given the recipients of a message by the creator of the
message, you may be able to reply to a message.
Conditional: To reply to the sender of a message, click
Reply.4
Conditional: To reply to all the recipients of a message, click Reply to
All.5
Conditional: To forward a message to others, click Forward.6
A message may be a reply to another message, which may itself be a reply to yet
another message, and so forth, going back to the initial message. This list of messages,
sorted in reverse chronological order, is a message thread.
Each message in a message thread has its own set of permissions. When
viewing a message thread in a Message Reader window or a Message Editor
window, the permissions of each message in a message thread must be
respected.7
This could result in conflicts; for example, suppose you want to perform one of the following operations:
For each of these operations, a message in the message thread may have a permission
setting that causes a conflict.
For example, suppose you want to print the contents of a message thread; however, a
particular message in the message thread has a disabled print permission. How should
this conflict be resolved?
Confinet resolves this conflict by allowing you to filter the messages in a message thread
by their permission settings.
For example, to print the contents of a message thread, select Display messages that
can be Printed. This filters out any messages in the message thread that cannot be
printed due to their print permission settings.
The following table displays permission-dependent operations and the filters that must be selected to enable these operations:
| Operation | Permission Filter |
| Copy the message to the clipboard | Copied to the Clipboard |
| Export the message to a text file | Exported to a Text File |
| Export the message to a PDF file | Exported to a PDF File |
| Print the message | Printed |
To perform an operation in the left column, select the matching filter in the right
column. These filters can be selected at the bottom of a Message Reader window (or a
Message Editor window).
From this point on, for the sake of simplicity, we may use the terms message and message thread interchangeably.8
(See figure 9.9)
In a Message Editor window, you can edit messages created by you for other
users.
To edit a message created by you:
You can update the contents of a message you have created, even after you have already sent
the message.9
After you update the contents of a message, the new contents will be displayed the next time the message is opened by one of the recipients of the message, even if the message is part of several message threads.
You can update the recipients of a message you have created, even after you have sent
the message.
If you remove a recipient, the next time the recipient opens a Message Browser window,
the message will not be displayed in the new Message Browser window.
By contrast, if you add a recipient, the next time the recipient opens a Message Browser window, the message will be displayed in the new Message Browser window.
You can update the permissions of a message you have created, even after you have sent
the message.
After you update the permissions of a message, the new permissions will be applied the next time the message is opened by one of the recipients of the message.
You can update the document attachments of a message you have created, even after
you have sent the message.
If you remove a document attachment, the next time a recipient views the
message in a Message Reader window, the document attachment will not be
displayed.
By contrast, if you add a document attachment to a message, the next time a recipient opens the message in a Message Reader window, the document attachment will be displayed.10
To delete a message:
Note: You cannot undo this operation.
If a message you have created is currently being referenced by another
message, you will not be able to delete it because it is still in
use.11
However, you can control the visibility of a message by enabling or disabling its view permission, irregardless of whether the message is being referenced by other messages.
(See figure 9.10)
In a Message Browser window, you can search messages using full text search and
several types of criteria.
To search for messages:
In a Message Browser window, you can organize your messages in message folders.
(See figure 9.11)
To create a message folder:
Note: Deleting a message folder will delete all of the messages contained in
it.
To delete a message folder:
Note: You cannot undo this operation.
A group is a collection of users with Confinet accounts. This chapter will discuss both home groups and personal groups.
When a Confinet Administrator creates a user account, the user is given a home group by
the Confinet Administrator. At any given time, a user belongs to exactly one home
group.1
A user must have a group key in order to have direct access to a home group; this includes the home group to which the user belongs.2
From a My Groups window, a user can create personal groups in order to make the distribution of documents and messages to other users more convenient.
You can create a personal group in a My Groups window.
To create a new personal group:
(See figure 10.3)
To add users to a personal group:
To remove a user from a personal group:
To delete a user group:
This chapter will discuss the display of pictures and images in Confinet documents and messages.
(See figure 11.1)
Confinet documents and messages can display the following types of images:
| Description | Format |
| Windows Bitmap | BMP |
| Graphic Interchange Format | GIF |
| Joint Photographic Experts Group | JPG |
| Portable Network Graphics | PNG |
To embed a reference to a picture inside of a document:
To embed a reference to a picture inside of a message:
When you embed a reference to a picture in a document or a message, you are
essentially embedding the name of a file containing the image in the document or
message.1
In addition, the pathname of the directory containing the image file is not embedded
with the name of the image file. Instead, the pathname of the directory containing the
image file is automatically added to a list of directory pathnames that the Confinet
Client application searches for image files.
But what happens if you move the image file to a new directory? How will the Confinet
Client application find the image file then?
The Confinet Client application handles this situation by allowing you to explicitly
specify the pathname of a directory containing images files. This allows you to specify
any location for your image files.
To add a directory to the list of directories searched for image files:
To edit the name of a directory in the list of directories searched for image files:
To remove a directory from the list of directories searched for image files: